A Guide to the Security of Critical Infrastructure (SOCI) Act (2018)

Table of Contents
- What is the SOCI Act 2018?
- Who does the SOCI Act apply to?
- History of the SOCI Act
- SOCI Act: Latest update 2024
- How to become SOCI compliant?
- Your roadmap to SOCI compliance
- Make your infrastructure SOCI-compliant with Macquarie Data Centres
Australia’s economy, security, and society depend on its critical infrastructure. But with the growing risk of cyber attacks, this critical infrastructure is becoming increasingly at-risk. In 2023, the Australian Cyber Security Centre (ACSC) received over 94 thousand cyber crime reports—marking a 23.7% increase from 2022 and a 57.2% rise since 2020. These statistics are nothing if not sobering.
The Security of Critical Infrastructure (SOCI) Act 2018 is part of The Federal Government’s efforts to address these risks. It is a robust framework to help Australia’s organisations patch vulnerabilities, improve security, and respond effectively to cyber attacks and hazards.
As a business, the SOCI Act outlines the legal obligations and requirements you need to meet if you own, operate, or have a direct interest in critical infrastructure. It also provides guidance around the Government assistance available should you suffer a breach or incident.
The SOCI Act is always evolving in response to new changes. That’s why we at Macquarie Data Centres have created this comprehensive guide to shed some light on what the Act entails and everything you need to do to comply as per the latest updates in 2024.
What is the SOCI Act 2018?
The Security of Critical Infrastructure (SOCI) Act 2018 is a mandatory framework for security compliance. The Act requires all entities that work with critical infrastructure assets and operate within a critical infrastructure sector to comply with obligations designed to safeguard their assets and uphold security standards.
How is ‘critical infrastructure’ defined?
Critical infrastructure in the context of the SOCI Act refers to any asset that is essential to the functioning of Australia’s national security, economy, or society. This includes IT systems, supply chains, and physical infrastructure that, if damaged or destroyed, could negatively impact the well-being of Australia or affect its ability to adequately protect itself from external threats.
Who does the SOCI Act apply to?
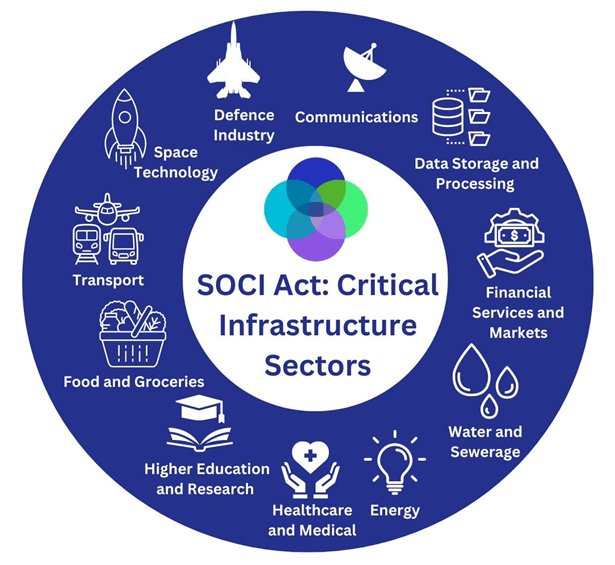
When it commenced in July 2018, the SOCI Act only applied to four critical infrastructure sectors: water, maritime ports, electricity, and gas. Since then, The Federal Government has expanded the Act with numerous reforms designed to strengthen the resilience of Australia’s critical infrastructure.
As a result, the SOCI Act now applies to 11 critical infrastructure sectors and 22 asset types. These include:
| Critical Infrastructure Sector | Critical Infrastructure Asset |
| Communications | Telecommunications Broadcasting Domain Name Systems (DNS) |
| Data Storage and Processing | Data Storage and Processing |
| Defence Industry | Defence |
| Energy Sector | Electricity Gas Energy Market Operator Liquid fuel |
| Financial Services | Banking Superannuation Insurance Financial Markets Infrastructure Payment Services |
| Food and Grocery | Food and Grocery |
| Health and Medical | Hospitals |
| Higher Education and Research | Education |
| Space Technology | Space Technology |
| Transport | Port Freight Infrastructure Freight and Logistics Services Public Transport Aviation |
| Water and Sewerage | Water and Sewerage Facilities |
In addition, the Government defines two types of entities that need to adhere to the SOCI Act’s requirements. These are:
- Responsible Entities: An entity that owns or is responsible for operating a critical infrastructure asset.
- Direct Interest Holders: An entity that holds a legal or equitable interest in 10% or more of a critical infrastructure asset. Or an entity that has an interest in the asset that puts them in a position to influence or control that asset directly or indirectly.
Know that the definitions of Responsible Entities and Direct Interest Holders are slightly different for each critical infrastructure sector. However, for general purposes, the definitions provided above are broadly applicable.
Does the SOCI Act apply to me?
To sum up, The SOCI Act will usually apply to you provided:
- You operate within one of the 11 industry sectors above.
- Your organisation fits the criteria as a Responsible Entity or Direct Interest Holder.
If you don’t meet both of those criteria, the SOCI Act may impact you indirectly, but you won’t need to take steps to comply with it.
Does the SOCI Act apply to multinational businesses?
The expanded SOCI Act means multinational businesses expanding to the Australian market will need to check whether the legislation applies to them.
Evolving data sovereignty laws mean compliance requirements are always evolving, so it’s crucial to stay abreast of the responsibilities if you are a multinational entering the country.
History of the SOCI Act.
The SOCI act was introduced as a component of Australia’s Cyber Security Strategy 2020—the resulting legislation that followed a string of enormous cyber attacks that exposed vulnerabilities in Australia’s critical infrastructure systems.
Since then, the Act has undergone several amendments and expansions. Here’s a brief overview of the reforms, events, and deadlines regarding the SOCI Act, as well as the latest information as of August 2024.
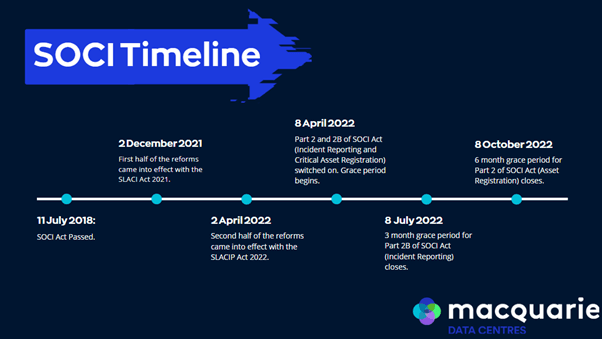
11 July 2018 – SOCI Act passed.
On 11 July 2018, the Australian Government enacts the Security of Critical Infrastructure (SOCI) Act to address risks to Australia’s critical infrastructure. The Act currently only encompasses four critical infrastructure sectors: water, gas, electricity, and maritime ports.
2 December 2021 – Part 1 of the Security Legislation Amendment (Critical Infrastructure) (SLACI) Act.
The first half of the two-part SLACI Act amends the SOCI Act to encompass a broader range of industry sectors (now 11 in total) and asset classes.
It also introduces several additional security and risk management requirements to combat evolving cybersecurity risks. This amendment includes the addition of positive security obligations (PSOs) to provide critical infrastructure entities with greater clarity over the SOCI Act’s requirements.
2 April 2022 – Part 2 and 2B of the Security Legislation Amendment (Critical Infrastructure) Protection Act (SLACIP).
Five months later, the second half of the two-part SLACI Act comes into effect, bringing with it new risk management requirements. In particular, it requires all responsible entities to maintain a risk management program to address cyber and physical threats. It also enforces mandatory cyber incident reporting for entities in critical infrastructure sectors.
Together with the December 2021 legislation, the SLACI Act builds what we now know as the modern Commonwealth framework for critical infrastructure protection.
8 April 2022 – Part of 2 and 2B of SOCI Act “switched on”.
Part 2 of the SOCI Act (Information Provision PSO) is switched on for 13 critical infrastructure asset classes. In addition, Part 2B of SOCI Act (Mandatory Cyber Incident Notification PSO) was switched on for the vast majority of critical infrastructure assets.
This began a six-month grace period for Part 2 and a three-month grace period for Part 2B, giving organisations time to achieve compliance.
8 July 2022 – Grace period ends for Part 2B of SOCI Act.
The three-month grace period for compliance with Part 2B (Mandatory Cyber Incident Notification PSO) of SOCI Act comes to an end.
8 October 2022 – Grace period ends for Part 2 of SOCI Act.
The six-month grace period for compliance with Part 2 (Information Provision PSO) of SOCI Act concludes.
17 February 2023 – Part 2A of SOCI Act “switched on”.
Part 2A of SOCI Act (risk management program PSO) switches on for 13 critical infrastructure asset classes. This introduces a requirement for responsible entities to adopt and maintain a critical infrastructure risk management program (CIRMP) that takes an “all hazards approach”. This began a 6-month grace period to help organisations achieve compliance.
17 August 2023 – Grace period ends for Part 2A of SOCI Act.
The six-month grace period for compliance with Part 2A (Risk Management Program PSO) comes to an end.
SOCI Act: Latest update 2024.
On 22 November 2023, the Australian Government released its 2022-2030 Australian Cybersecurity Strategy as part of its desire to become a world leader in cybersecurity by 2030.
Along with this strategy comes several proposed amendments to the SOCI Act that are coming to fruition. These proposals are outlined in the 2023-2030 Australian Cyber Security Strategy: Cyber Security Legislative Reforms Consultation Paper.
Crucially, the Government has identified numerous gaps in the SOCI regulation’s coverage. For instance, it now intends to clarify the Act to ensure critical infrastructure entities are properly safeguarding their data storage systems.
The most pressing update for 2024 is the arrival of the Australian Government’s deadline for the Government’s Critical Infrastructure Risk Management Program (CIRMP) annual report. Every responsible entity must now provide a yearly CIRMP report to the Australian Department of Home Affairs (DHA), with the first reports due by 28 September 2024.
Among other reforms, the Government also hopes to streamline telecommunications security regulations by transferring them from the Telecommunications Sector Security Reforms (TSSR) over to the SOCI Act. They also hope to further clarify the security obligations of managed service providers under the Act to better protect personal information.
In short, the SOCI Act isn’t going anywhere anytime soon. And with cybercrime growing year-on-year, the Government is set to tighten restrictions and continually amend the Act to protect national interests. The goalposts may never stop moving.
This effectively means organisations within critical infrastructure sectors will need to chase a moving target. It’s vital to stay abreast of the Government’s requirements and remain agile so you can adapt to regulatory changes.
How to become SOCI compliant?
If you operate within a critical infrastructure sector and are either a Responsible Entity or Direct Interest Holder, there are three positive security obligations (PSOs) you’ll need to meet for compliance. These are:
- Register of Critical Assets PSO.
- Risk Management Program PSO.
- Mandatory Cyber Incident Notification PSO.
Additionally, if your critical infrastructure assets are Systems of National Significance (SoNS)—meaning the asset is deemed ‘most crucial’ to the nation—there are four additional Enhanced Cyber Security Obligations (ECSO) to meet.
Let’s break down every requirement in greater detail.
Register of critical assets PSO.
The responsible entity for a critical infrastructure asset must register its assets by providing operational information (who/what it serves) and contact details. This also involves offering information about the asset’s core functions and business-critical data, such as personal or protected information.
In addition, a Direct Interest Holder for a critical infrastructure asset must provide interest and control information to the secretary of the Department of Home Affairs.
This obligation is ongoing. If the information becomes inaccurate or incomplete at any point, the Responsible Entity or Direct Interest Holder must notify the secretary and provide steps to correct or complete it.
Risk management program PSO.
With the 6-month grace period for Part 2A of the SOCI Act concluding on 17 August 2023, all responsible entities must now adopt, maintain, and comply with a critical infrastructure risk management program in line with CIRMP rules.
This risk management program must adopt an “all-hazards” approach to the critical infrastructure asset. It should:
- Identify all potential hazards where there is a risk of relevant impact.
- Eliminate, mitigate, or minimise the risk from each identified hazard (to the maximum reasonable extent).
Hazards can be either naturally occurring or man-made and may include cyber risks, personnel, supply chain concerns, physical security, and natural hazards (such as disasters).
In particular, the risk management program should establish a process for complying with the Essential Eight Maturity Model, ISO/IEC 27001, or another equivalent framework for information security.
Mandatory cyber incident notification PSO.
Part 2B of the SOCI Act introduced a new PSO for responsible entities to report cyber security incidents.
This means all responsible entities must report any cyber security breaches to help the Australian Government build an aggregated threat picture of cyber security risks.
What constitutes a cyber security incident? The SOCI Act defines it as unauthorised access to data or the impairment of infrastructure. These incidents are further classified into two levels of concern:
- Critical cyber security incidents: Caused/causing a significant impact on the critical asset’s ability to deliver services. Must be reported within 12 hours of detection.
- Other cyber security incidents: Caused/causing a relevant impact on the critical asset’s availability, reliability, or integrity. Must be reported within 72 hours of detection.
To report an incident, the responsible entity must contact the ACSC verbally or in writing. All responsible entities must comply with this obligation within 3 months after the asset is deemed ‘critical infrastructure’.
Enhanced Cyber Security Obligations (ECSO).
A responsible entity for a system of national significance must also meet additional ECSO requirements. Here’s a brief overview of what these requirements entail:
- Cyber security: Carrying out cyber security exercises that test the entity’s ability to respond and prevent cyber incidents. Examples include reporting and external audits.
- Incident response: Adopting and maintaining robust incident response plans for the asset.
- Vulnerability assessments: Undertaking vulnerability assessments to identify security weaknesses and potential solutions.
- Periodic updates: Providing system information to the Australian Signals Directorate (ASD) to help maintain a real-time threat picture.
For systems of national significance, these SOCI Act obligations will apply from the date set by the declaration.
Your roadmap to SOCI compliance.
There is no shortcut to SOCI compliance. Every critical infrastructure sector has unique requirements, and achieving the SOCI Act’s strict legislation demands a concerted organisation-wide effort.
1. Align your board on SOCI requirements.
A good place to start is to align your key stakeholders and leaders on SOCI. Ensure that everyone understands what the legislation entails and the steps to reach compliance.
In addition, we suggest appointing a senior executive to oversee SOCI compliance from the top down. You may also employ representatives for each department to coordinate organisation-wide efforts.
2. Develop your register of CIAs.
It’s essential to build and maintain a register of all critical infrastructure assets. This register should contain all vital information related to your assets, such as what they are and who they serve. This falls under the Register of Critical Assets PSO, and it can also help with proactive risk management strategies.
The Cyber and Infrastructure Security Centre (CISC) provides further guidance on creating and maintaining your register in accordance with the PSO.
3. Evaluate your risk.
As mentioned, all responsible entities must follow an “all hazards” approach. You need to be able to identify and respond to several types of hazard vectors, including:
- Cyber and information security risks.
- Physical and natural risks.
- Personnel (insider threats).
- Supply chain disruptions.
Conduct a thorough risk assessment to identify all hazards that could have a relevant impact on your critical infrastructure. Evaluate the likelihood of each hazard occurring, and remember to maintain this document as new threats emerge. These findings will form the basis of your CIRMP.
4. Take steps to mitigate or eliminate those risks.
Next, you’ll need to implement safety and risk management protocols organisation-wide to remove or reduce your identified risks.
To break down possible risk management strategies, here is an overview of how to mitigate risks for each of the four core hazard vectors.
Cyber and information security hazards.
To eliminate or mitigate cyber and information security risks, you might:
- Train employees to recognise malware and phishing risks.
- Implement robust cybersecurity measures to reduce the risk of cyber incidents.
- Regularly test your cybersecurity measures through penetration testing.
- Enforce correct access privileges to critical systems.
- Ensure access controls are updated regularly.
- Develop an incident response plan detailing the actions to take in response to a cybersecurity threat.
Physical and natural risks.
To eliminate or mitigate physical and natural risks, you could:
- Employ security to patrol and monitor your SOCI critical infrastructure.
- Install CCTV to help detect unauthorised access.
- Use access controls to lock down fire alarms, cameras, and HVACs from attacks.
- Implement robust physical access controls, like biometric key cards and perimeter fencing.
- Create clear contingency plans, emergency drills and simulations to prepare staff for natural risks, such as bushfires.
Personnel hazards.
To eliminate or mitigate personnel hazards, such as the risk of an insider threat, you may:
- Take steps to enforce proper access controls—both physical and digital.
- Screen critical workers and perform background checks before hiring employees.
- Improve on-site monitoring capabilities, such as CCTV, to monitor critical personnel.
- Provide cyber security training to staff to mitigate the risk of phishing.
Supply chain hazards.
To eliminate or mitigate supply chain hazards, you could:
- Identify dependencies on supply chain bottlenecks and work to reduce these dependencies through diversification.
- Ensure all suppliers that can access sensitive data have effective security and cybersecurity policies built into contract agreements.
5. Build and implement your CIRMP.
With an understanding of your risks, you can now construct your CIRMP. For each identified risk, you must outline how you are taking steps to minimise or eliminate that risk as much as is reasonably practicable.
A CIRMP is very much an ‘ongoing program’. It’s important to regularly iterate, especially with the requirement for responsible entities to send an annual CIRMP to the Department of Home Affairs (DHA).
6. Partner with a secure, sovereign data centre.
Data is at the core of SOCI compliance because, ultimately, it is one of the most important critical infrastructure assets to keep secure.
Sovereign data centres have become increasingly important in recent years as a way to keep sensitive data onshore, secure against cyber threats, and compliant with Australian laws.
Even for businesses that operate on a cloud or hybrid-cloud model, physical IT infrastructure is often the first point of access to disrupt operations and steal data, so it’s important to establish a dependable line of defence. A sovereign data centre is one of the most important cogs in managing risk and achieving compliance with the SOCI framework.
Make your infrastructure SOCI-compliant with Macquarie Data Centres.
At Macquarie Data Centres, we’ve built our entire model through customer centricity, which is why we’re always looking to achieve the highest standard of security and compliance.
In fact, we’re one of the most heavily-certified data centres in the world. There’s a reason we’re trusted to safeguard the critical IT infrastructure of 42% of all Australian Federal Government operations. That means you can feel confident that our colocation solutions are built to protect and secure your critical infrastructure assets.
As a leading pioneer in the Australian Data Centre industry, our sovereign and secure facilities are built for scale and adaptable to provide the ideal environment for your business requirements. Learn more about our secure, sovereign, compliant data centres, or enquire now to ask us any questions you may have.
Read more about our colocation services in Sydney and Canberra.
Read more about our data centres in Sydney, Macquarie Park, and Canberra.




